The most DevOps pipelines use variables to store credentials and other variables. With DevOps you have the possibility to hide/encrypt data, but in an enterprise environment mostly KeyVaults are in use to store the sensitive data in a central store to provide better management. This post is to show you how you can use a KeyVault and use passwords in your pipeline. This post referrers to my last blog post and uses this pipeline.
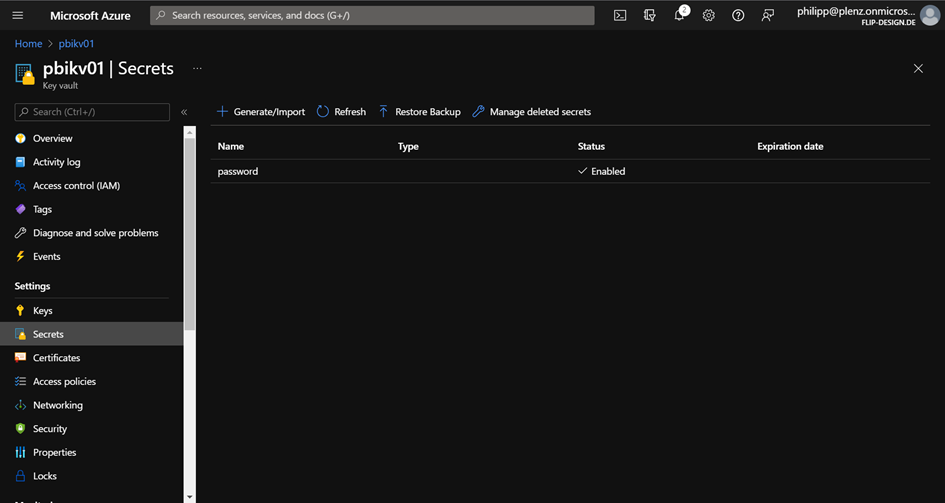
To start, I created an Azure KeyVault and I store inside a password which is able in combination with the username to start a Power BI deployment pipeline.
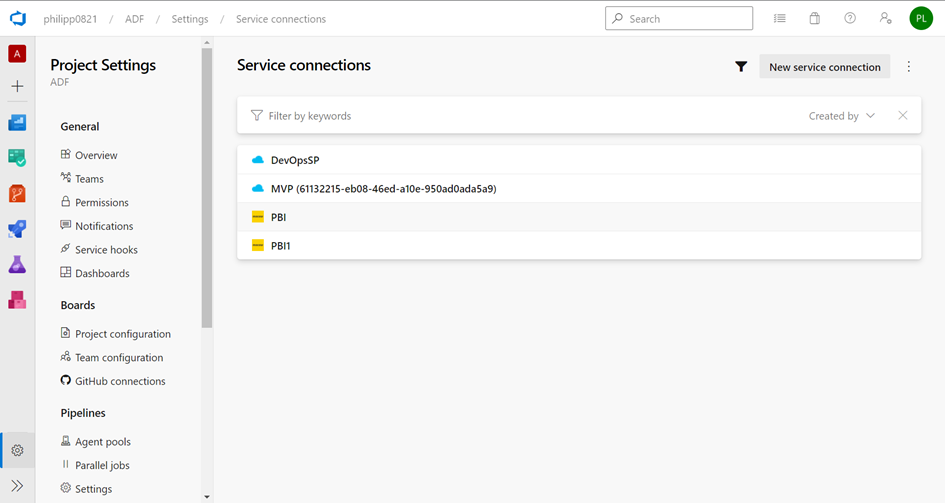
Next, you need to create a service connection to your Azure tenant:
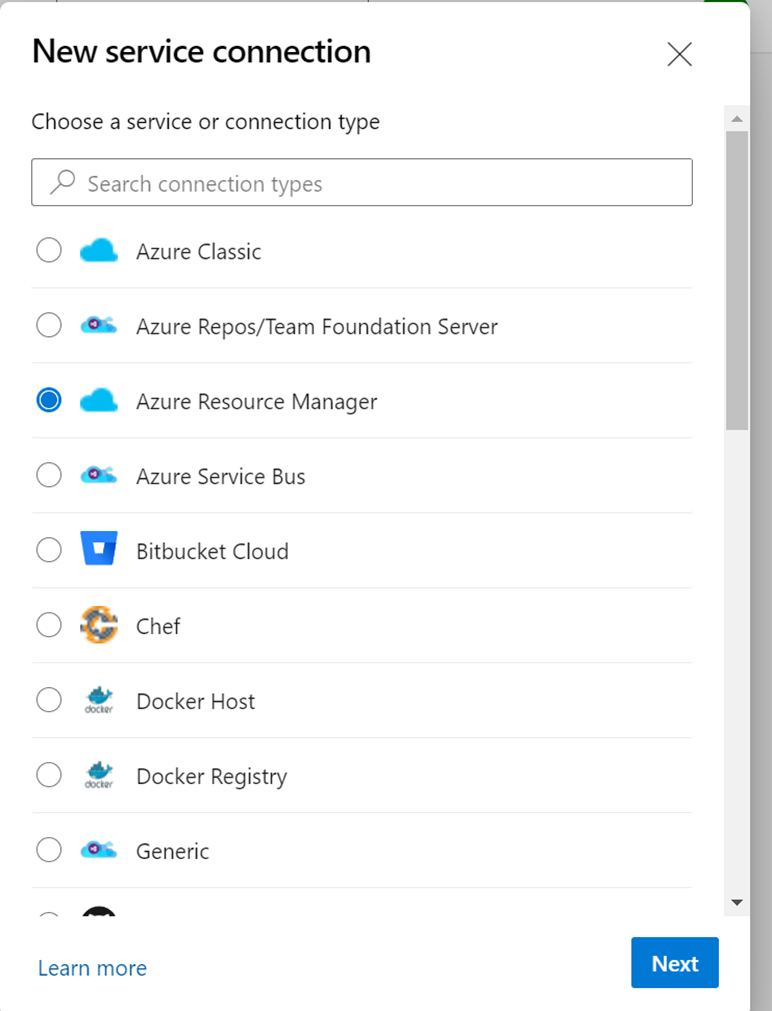
Select Azure Resource Manager
Select service principal
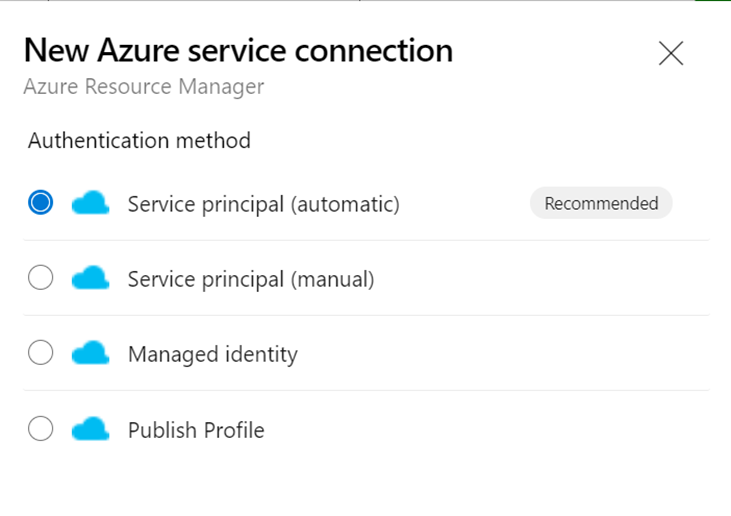
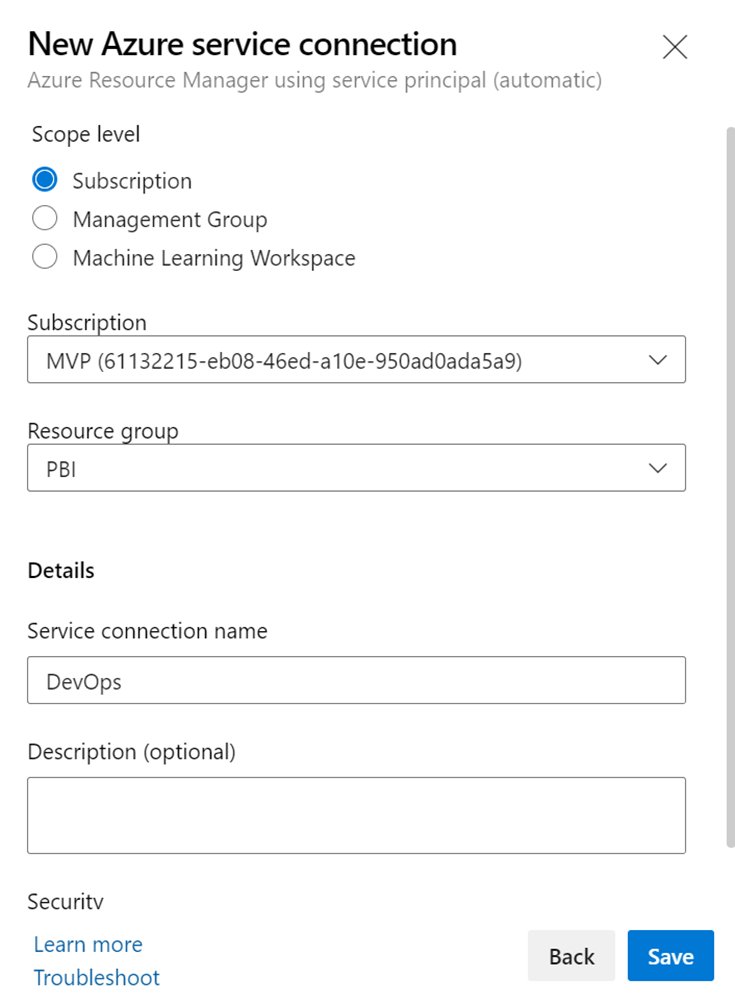
Select your subscription and the Resource Group where the KeyVault is stored
After creating your Service Principal, you can get the name of it by clicking to the Manage link
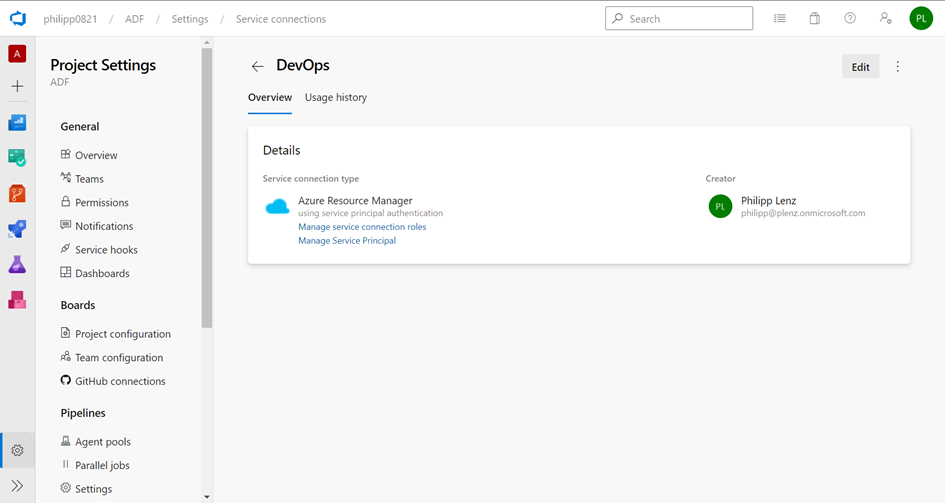
After clicking at ServiePrincipal, you will get the name of it, and your can add the Access Policy:

Select Get and List to get the Secrets and the content
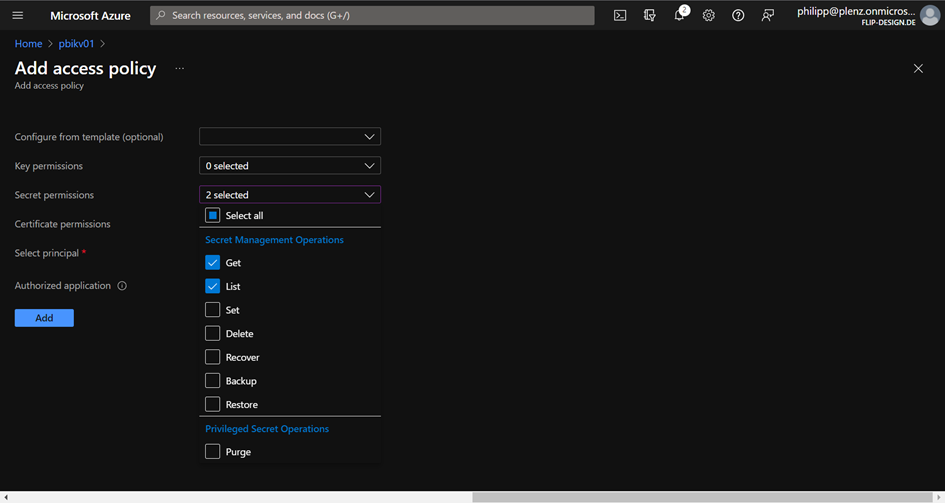
Add your Service Principal which was created by DevOps

Don’t forget to click Save. Next, back to Azure DevOps and refer to Library. Here you can add a new variable group which uses your KeyVault.
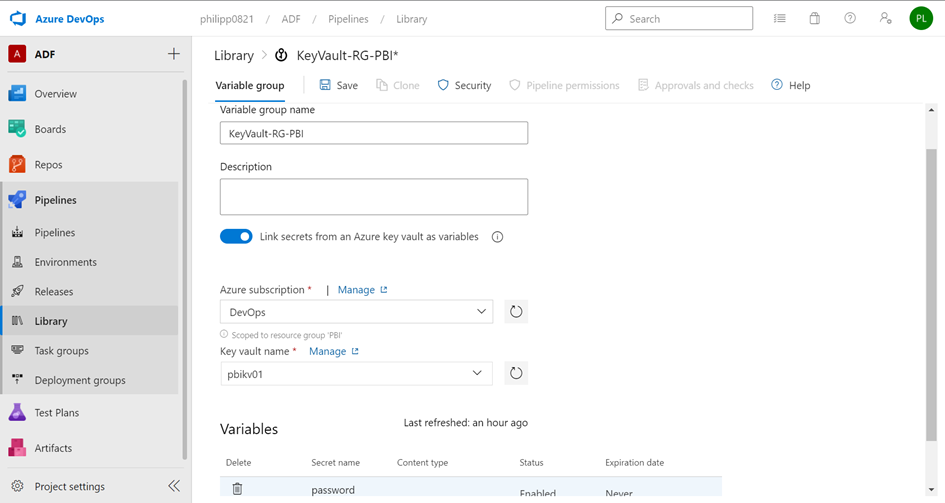
You need click to Authorize to enable the connection. Next, you must go to your pipeline variables and add the newly created library

Inside your tasks you can use these variables. If your passwords contain some special characters, please put them into single quotes.


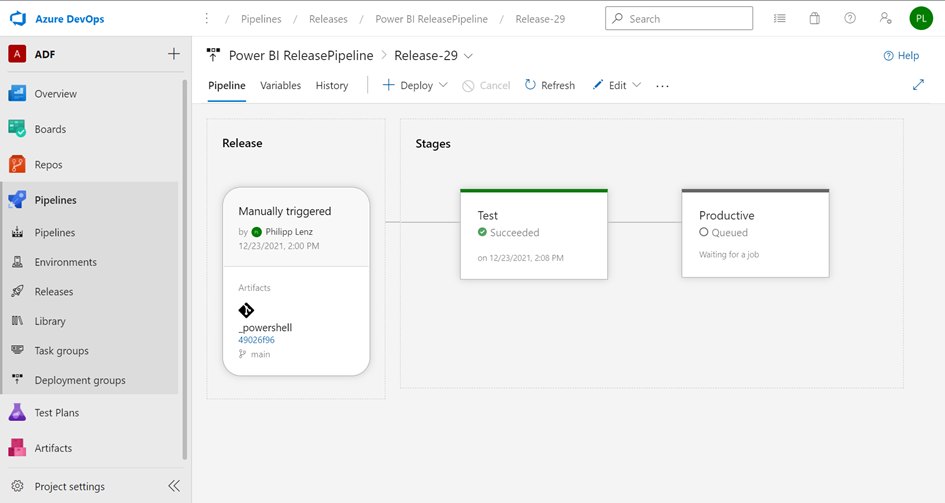
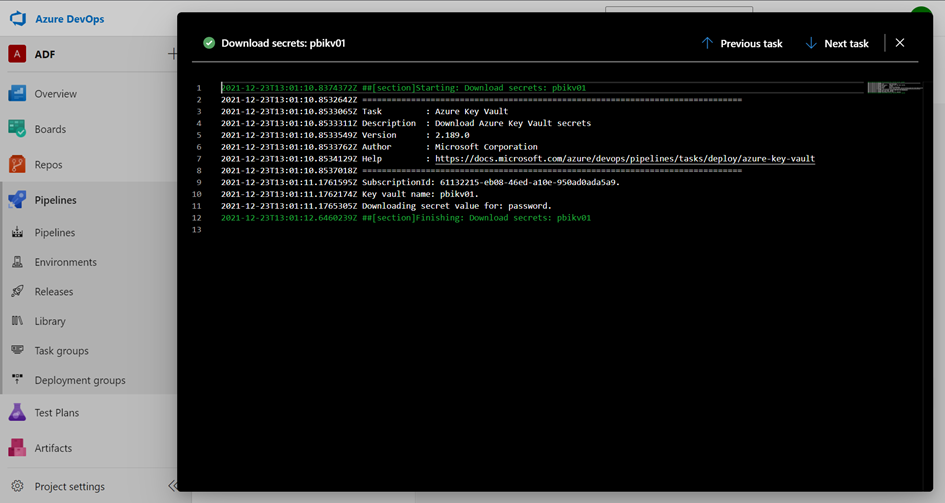
By viewing the results, you can see the using of the KeyVault